Hello Everyone !
In the previous article, I explained the installation of the Active Directory structure which we prepared for pentest. In this article, we will collect information about this structure without using a tool.
PowerShell is a new generation command line application developed as an alternative to Windows command line cmd.exe and Windows Script Host. The target here will be to collect information over the target Active Directory structure via PowerShell.
The purpose of this article is to gather information using Windows features without using tools. Since the text is long, I divided it into several other headlines;
- For Domain and Forest, Recon with .NET
- For Users, Recon with WMIC
- For Organization Unit and Groups, Recon with Active Directory Powershell Module
Let’s start !
Recon with .NET
PowerShell was developed as a management interface by combining command line and script language based on .NET framework. This situation did not only benefit system engineers… It also worked for us pentesters.
For example, in some Active Directory structures, there are times when you do not have access to PowerShell cmdlets. With the emergence of a platform where developers can use script capabilities, you are able to collect information about the target structure of some commands and modules used.
In this subtitle of the article, we will collect information about Forest and Domain in the target Active Directory structure with .NET.
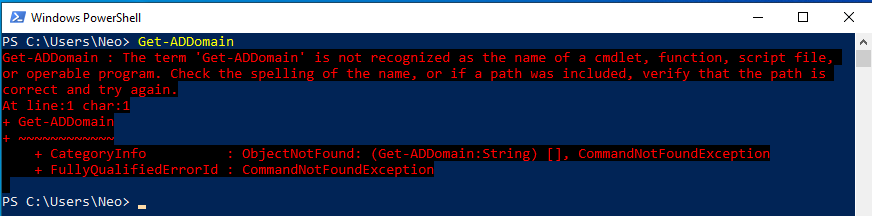
I wanted to get information about matrix.local in Active Directory structure with the command. However, the command was not recognized because the “activedirectory” module was not installed.
If the module called “Microsoft.ActiveDirectory.Management” is loaded, we can use this type of Active Directory commands. Let’s discuss this in the last subtitle… 🙂
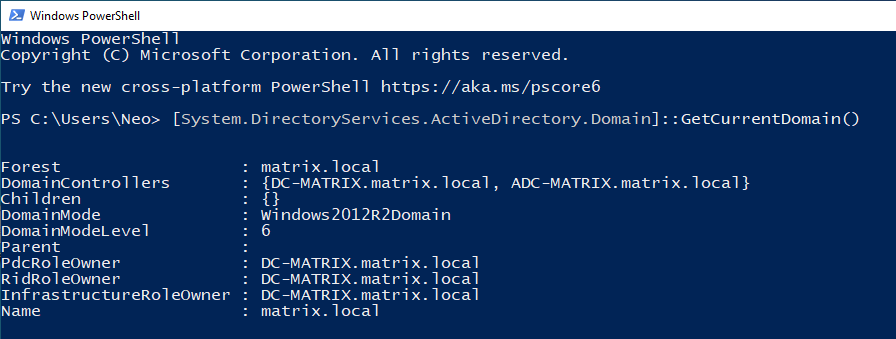
A complex .NET domain object that System.DirectoryServices.ActiveDirectory.Domain will return information about the domain similar the above if computer can reach a domain controller.
You can use it to learn specific information in the table below. Just add it to the end of the function… For example, If you add the “.Name” command to the end of the GetCurrentDomain(), you can get only the domain name as output.
| NAME | DEFINATION |
|---|---|
| Forest | Represents an Active Directory Domain Services Forest |
| DomainControllers | Represents the domain controller in an Active Directory domain |
| Children | Retrieves domains that are children of this domain |
| DomainMode | Indicates the operating mode on a domain |
| DomainModeLevel | Gets the level of mod running above this domain |
| Parent | Gets the parent of this domain |
| PdcRoleOwner | The primary domain controller (PDC) for this domain |
| RidRoleOwner | The domain controller that holds the relative identifier (RID) master role |
| InfrastructureRoleOwner | Represents the domain controller holding the infrastructure owner role |
| Name | Domain Name |
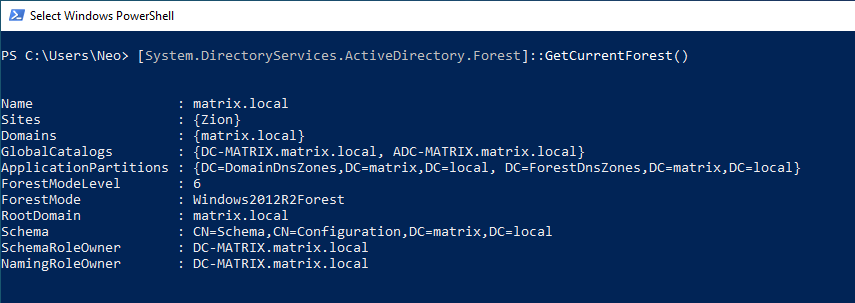
If you want to get information about the valid Forest structure, you can use the GetCurrentForest() function. Since there is only one domain in our Forest structure, the value of “matrix.local” is given to us.
| NAME | DEFINATION |
|---|---|
| Sites | Gets a collection of sites in the Forest |
| Domains | Gets a collection of all domains in the Forest |
| GlobalCatalogs | Retrieves a collection of all public catalogs in the Forest |
| ApplicationPartitions | Gets the collection of all application sections in the Forest |
| ForestModeLevel | Operating mode level of the Forest |
| RootDomain | Gets the first domain created in a Forest |
| Schema | Scheme of the Forest |
| SchemaRoleOwner | Domain holding the schema master role |
| NamingRoleOwner | Domain holding the naming master role |
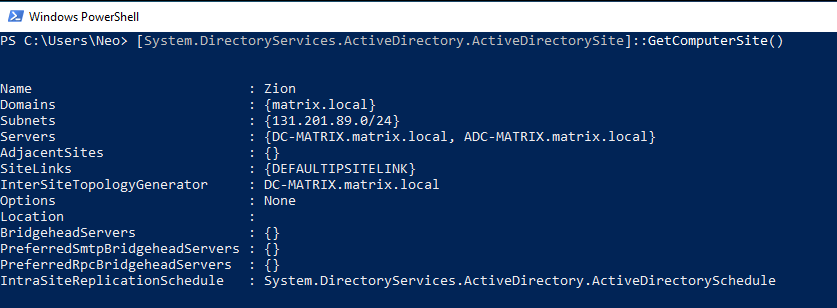
If Active Directory organization needs to serve branches in different physical regions, the Sites help you in this regard. You remember, I created only one Site in previous article.
With ActiveDirectorySite class, you can list the Sites within our structure. By using the GetComputerSite() function, you will list the Site which the computer named CLIENT-MATRIX is a member.
The name of the Site, the NID of the Site and the name of the servers on the Site are important in the output given.
| NAME | DEFINATION |
|---|---|
| Subnets | Returns subnets on the Site |
| Servers | Returns subnets on the site |
| AdjacentSites | Sites linked to a common sitelink with this site object |
| SiteLinks | Sitelinks with this site |
| InterSiteTopologyGenerator | Directory server serving as a cross-site topology generator |
| Location | Gets or sets the Site’s location |
| PreferredSmtpBridgeheadServers | Preferred bridgehead server for SMTP transport |
| PreferredRpcBridgeheadServers | Preferred bridgehead server for RPC transport |
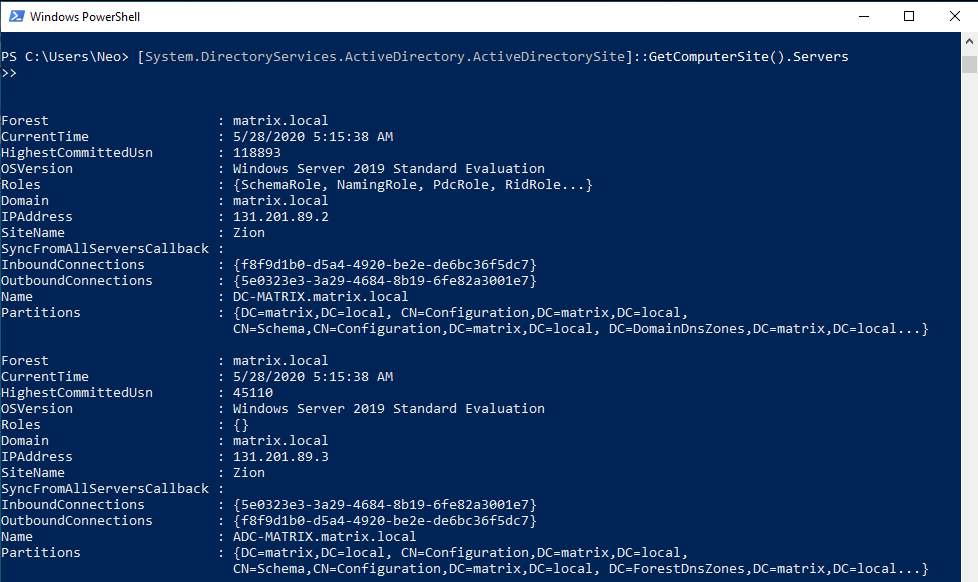
Let’s add the “Servers” method in addition to previous command. You were able to get information about the servers on the site named “Zion”.
When the output is analyzed, we have accessed some important information such as IP addresses, roles, operating systems of the servers.
| NAME | DEFINATION |
|---|---|
| CurrentTime | Current date and time from DC |
| HighestCommittedUsn | Gets the highest update sequence number registered on DC |
| Roles | Gets the roles that DC |
| IPAddress | IP address of DC |
| SyncFromAllServersCallback | Gets or sets the synchronization delegate for DC |
| InboundConnections | Inbound replication connections for DC |
| OutboundConnections | Outbound replication connections for DC |
Thanks to .NET, we were able to obtain the important information about the target Active Directory structure. You can analyze many functional commands from the address below.
Using Active Directory .Net methods in PowerShell Part 1
Using Active Directory .Net methods in PowerShell Part 2
WMI Command-line (WMIC)
WMIC is a command-line tool designed to ease WMI information recovery about a system by using some simple keywords (aliases).
Wikipedia
Windows Management Instrumentation is a technology that enables control of most objects and can perform operations and administrative functions in the operating system. With WMI, we can locate objects in an AD structure and collect information from them.
Since WMIC is a very comprehensive tool, we will only use this article to enumerate users and groups. But in the articles which I will publish in the future, I will also touch on the post exploitation part of the tool and practice on the lab.
Let’s start !
wmic [alias] [where clause] [verb clause]
WMIC has three basic keywords. These are alias, where clause and verbclause. In this way, you can direct your query and find the values specifically.
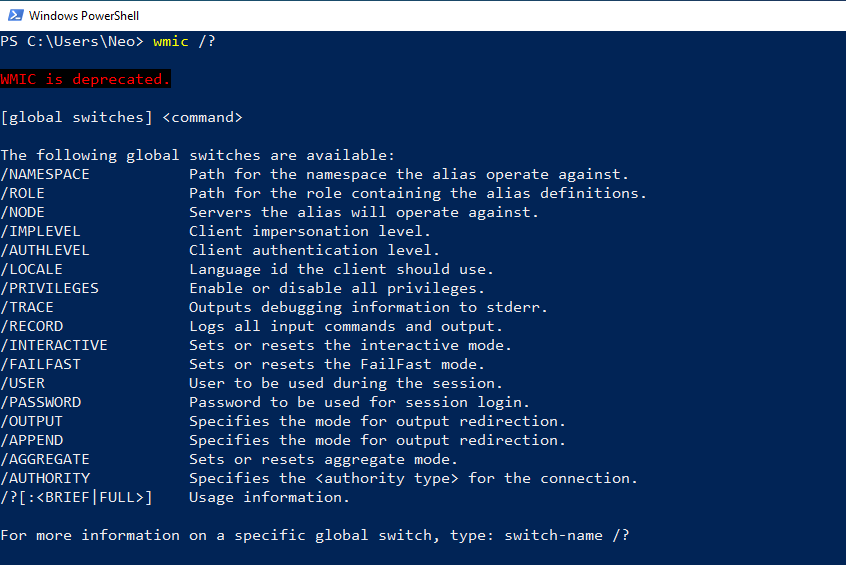
Using the “wmic /?”, you can get help on the commands that can be used.
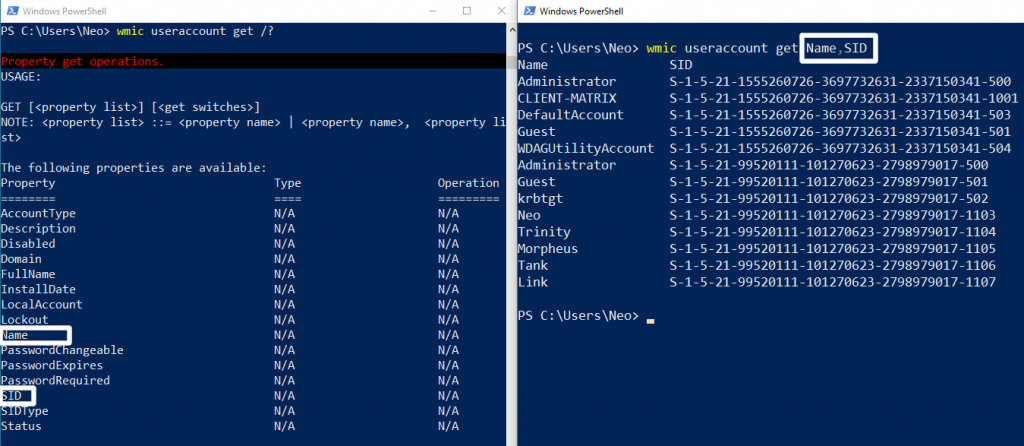
I gave an example to better understand the grammer structure of the command line. I used useraccount as alias in the picture on the left. Then I determined the method I want to query using a usage.
Again to make it specific “/?” I am learning properties using the command. For example, I used Name and SID. So I was able to perform a simpler query.
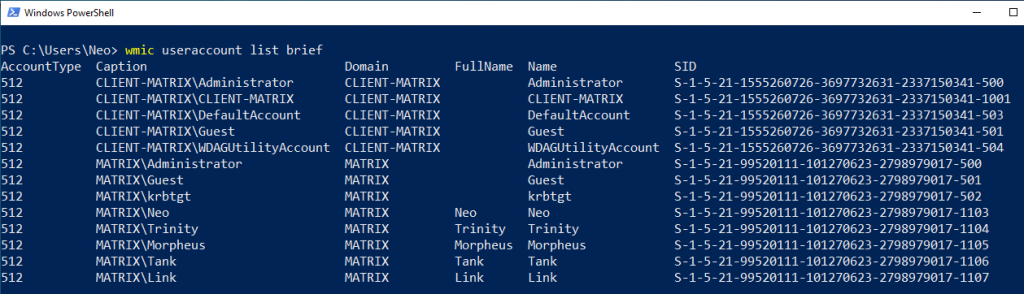
You can use the “list brief” command for both simple and detailed inquiry.
Let’s analyze the some properties.
1- AccountType:
This property lets you know what kind of account it is. We currently see only one value associated with this property. 512…
512 is the default or normal account of a typical Windows user. This is what you normally see when you execute the command given above. If the primary accounts were local user accounts in another Domain, we would see this value as 256. These accounts would only have access to that domain, not another domain. 2048 is a system domain account that also trusts other domains.
If you want to analyze in detail and learn other account types, I can recommend the website below.
http://www.selfadsi.org/ads-attributes/user-userAccountControl.htm
Attributes for AD Users : userAccountControl
2- Caption:
If you anaylze Figure – 8, the caption seems to be a combination of Domain and Name. We see that there are two different Domain structures. One is MATRIX and the other is CLIENT-MATRIX.
First, I will review CLIENT-MATRIX. Users in CLIENT-MATRIX are Local Accounts. Administrator, Guest, and DefaultAccount users are he default users that come when installing Windows. The user named CLIENT-MATRIX is the user we created when we first installed Windows 10.
You can review the detailed information about the users in the local group at the address I have given below.
https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/local-accounts
Local Accounts
Another structure is the users in the “matrix.local” domain, as you know. We created the users Neo, Trinity, Morpheus, Tank and Link in the previous article. I would like to draw attention to the two users here.
You can see two types of Administrator accounts. One of them is in CLIENT-MATRIX and the other is in matrix.local. To summarize, the Administrator account in CLIENT-MATRIX can only access in the Local group on that computer. However, the Administrator user on matrix.local can access all the computers on the domain. Here I will tell the details of this when I gather information about the groups.
Actually, I could change the name of one of the Administrators, but I thought it would be more useful to do so. Because we analyzed the difference. 🙂
Another user I would like to draw attention to is krbtgt. It’s created default when a new domain is created. It cannot be deleted, enabled and its name cannot be changed. Kerberos is an authentication protocol that allows the client to authenticate to the server with tickets.
The Kerberos user ticket lifetime must be limited to 10 hours or less… With the Golden Ticket transaction, the KRBTGT service account in the domain can increase this time by using the password summary and some information in the domain. To summarize, KRBTGT is actually a Kerberos service.
3- Security Identifier (SID)
We know that there are Domains in the Forest structure we created in Active Directory. There is an ID number assigned to each Domain. This is called Security-Identifier(SID). Also, we need to mention is the Relative-Identifier (RID). We can create objects in Active Directory. There are also ID values assigned for each of these objects created. These ID numbers are unique and are assigned at the time of creation.
Let’s analyze this unique ID number together.
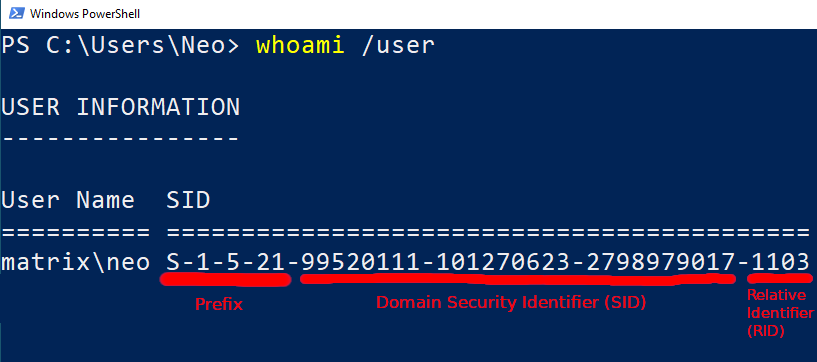
In Figure – 9, you can see the SID value of Neo in “matrix.local”.
- The letter S in the prefix part means “SID”.
- “1” is fixed value
- “5” means identifier authority. A value of 5 means that NT Authority
- “21” means sub authority indicating class of ID. A value of 21 means that the SID is not unique.
- The value in the SID is a unique ID number of the domain named MATRIX.
- The RID value is an number representing the user Neo.
If we analyze Figure – 8 again, RID values of local admin and domain name are 500 by default. But SID values are different because they belong to different domains. Also, we can see that the users named Trinity, Morpheus, Link and Tank have only different RID. Because they are located in the same domain (matrix.local).
You can find detailed information about SID values in the link I have given below.
https://docs.microsoft.com/en-us/windows/win32/secauthz/well-known-sids
Well-known SIDs
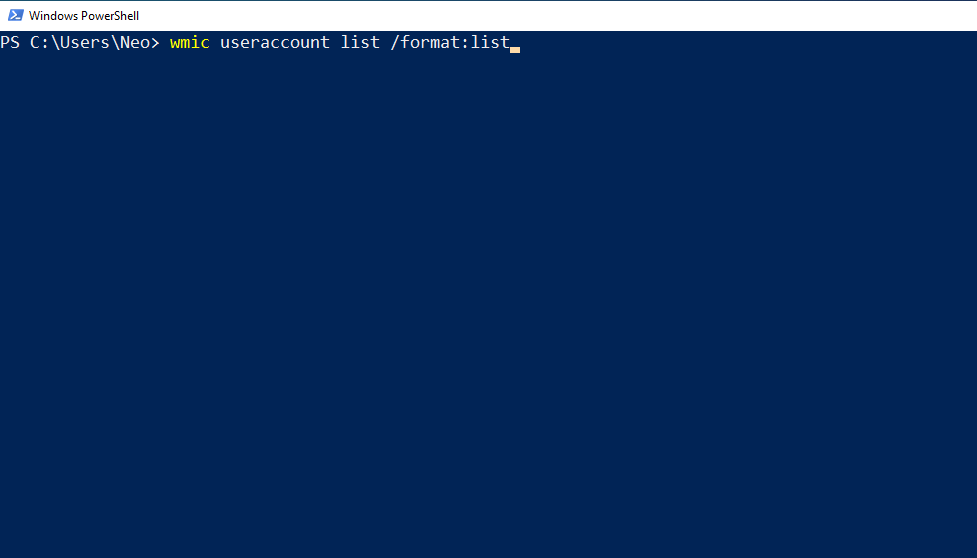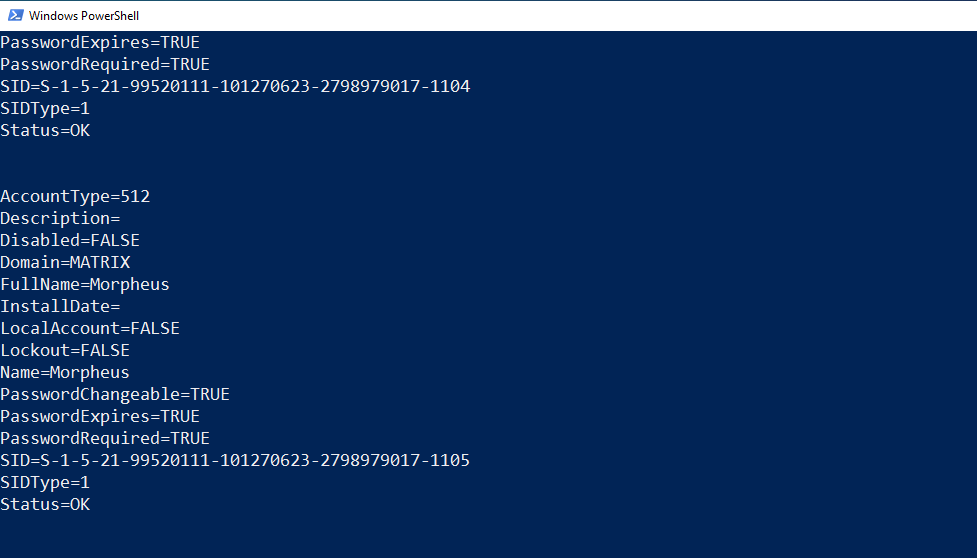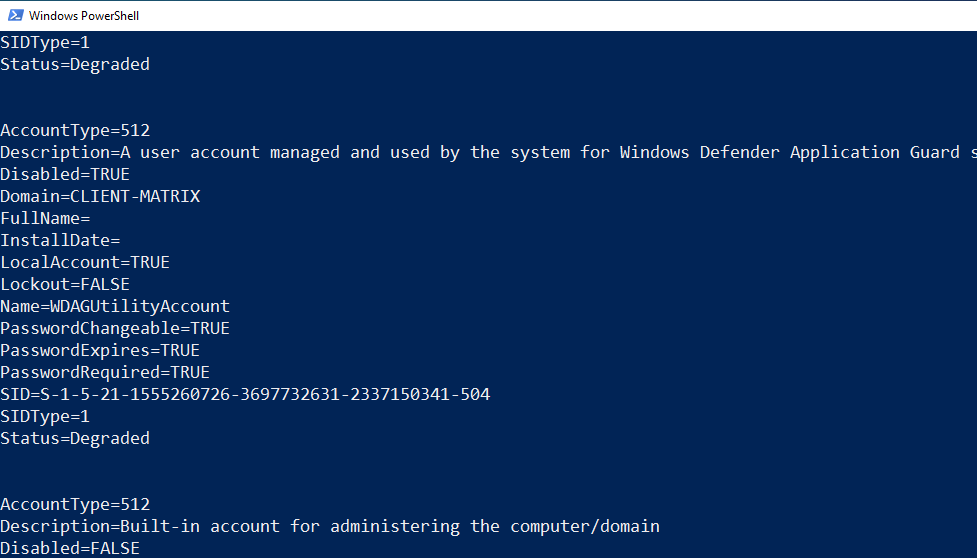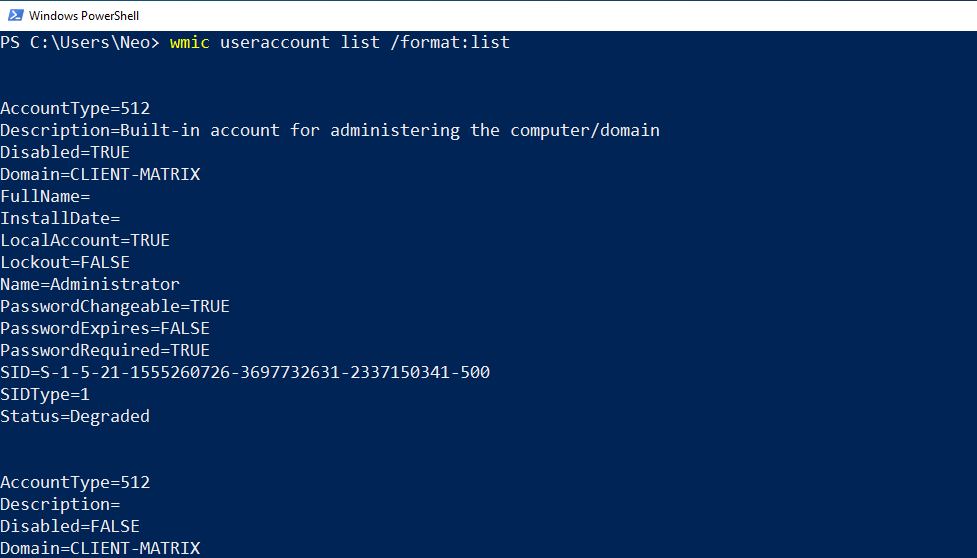
wmic useraccount list /format:list
Thanks to the command above, you can find out whether the password of the user account can be changed, expired or whether a password is required.
You can learn a lot of information about the users, such as their privileges, password policies. But without going into detail, we will collect information about another object in the Active Directory. Groups…
Let’s imagine a big company… Imagine that there are hundreds of employees here. It’s hard to manage user accounts and computers that belong to so many employees. Also, when other objects such as printers are involved… Thanks to the Group object, the management of other objects that becomes easier.
For example, groups can centrally and collectively manage the resources access and permissions of users that have been shared on the network.
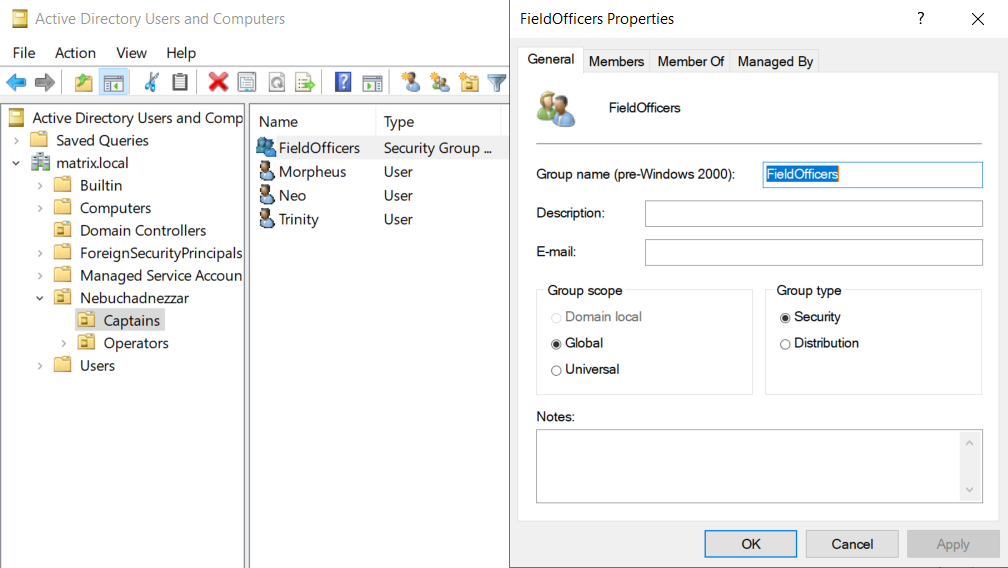
In the screenshot above, there is a sample group which we created in DC-MATRIX. By the way, this screenshot was taken over DC-MATRIX. If you remember, we added Neo, Morpheus and Trinity as members of FieldOfficers in the previous article. We can see that the group type is selected as Security Group. This group type permits resources on the system. The fact that Group Scope is Global can be seen both on its own domain (matrix.local) and on other domains with trust configured. In other words, this group with trust relationship can access other domains.
We did this review via DC-MATRIX. Now, let’s collect information about groups by using the properties of WMIC over CLIENT-MATRIX.
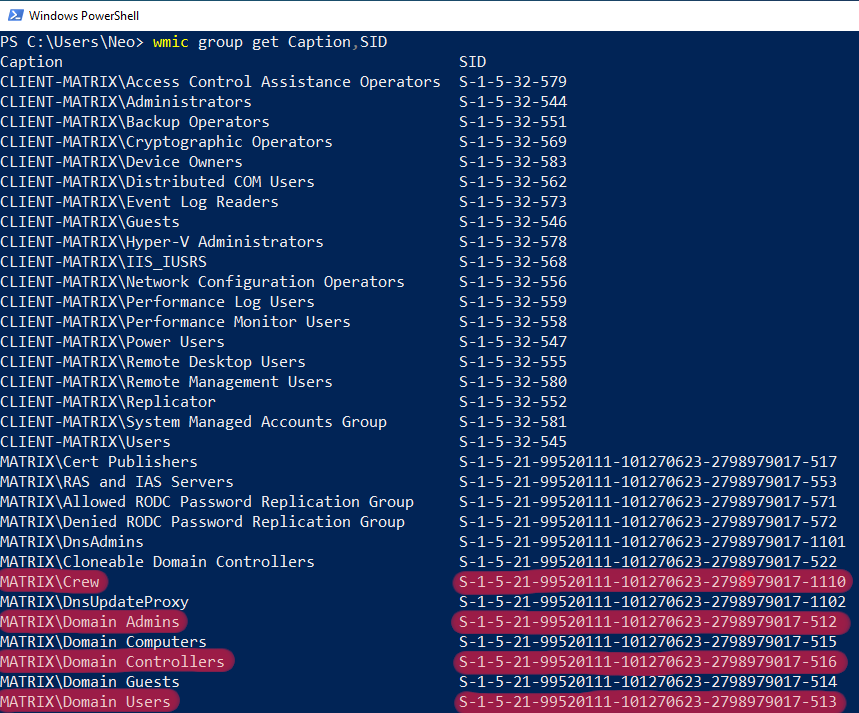
CLIENT-MATRIX and matrix.local groups are listed in the output after the command. I want to draw attention to 4 different groups. Crew, Domain Admins, Domain Controllers and Domain Users…
Crew was a group we added when we installed our Active Directory structure. If you remember, there were two users in this group. I will show these users on the Active Directory Management Module subtitle.
The Domain Users group lists all users in the domain. In Figure – 8 we were able to list all users of matrix.local.
The Domain Controllers group is the DCs of matrix.local in the Active Directory structure. In Figure – 2, we were able to list Domain Controllers via .NET.
And the Domain Admins group… Users who are members of this group are authorized to manage the Domain. For example, our user who is a member of our Domain Admin group is the Administrator that comes by default. I can summarize the importance of this group with the quote that I have given below;
The Domain Admins group controls access to all domain controllers in a domain, and it can modify the membership of all administrative accounts in the domain.
Domain Admins
You can reach detailed information about the groups from the link I have given below.
Active Directory Security Groups
At the end of this title, we collected information about users and groups. Let’s analyze the last title, Micorosft’s PowerShell ActiveDirectory module.
Active Directory PowerShell Module
Since Active Directory Management module is not installed in Figure – 1, we could not use the command. Can we not import this module manually? Yes, we can !
Thanks to the Microsoft.ActiveDirectory.Management.dll module We can recon Active Directory structure without RSAT and administrative privileges.
Let’s first add this module to CLIENT-MATRIX.
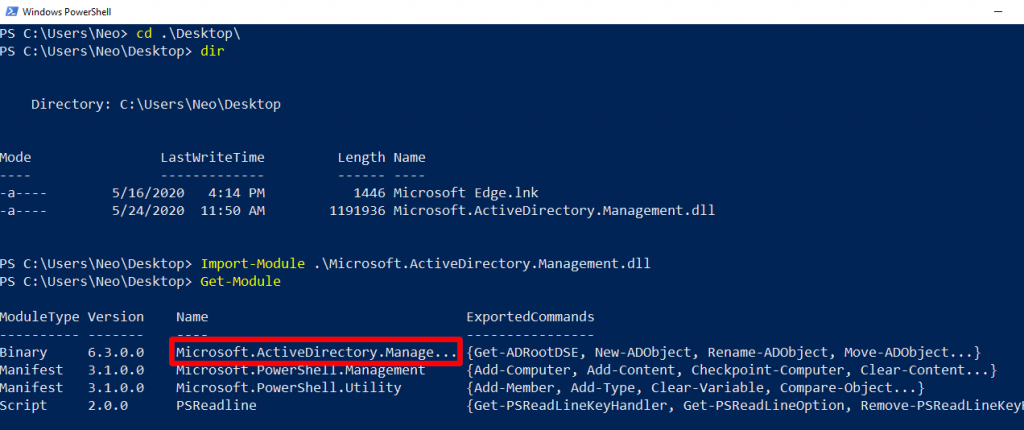
You can find Microsoft.ActiveDirectory.Management module in DC in the directory which I have given below.
C:\Windows\Microsoft.NET\assembly\GAC_64\Microsoft.ActiveDirectory.Management
Microsoft.ActiveDirectory.Management.dll
You cannot find it in Client because this module is available on servers (like DC). If the client is connected to the internet during the local network test, you can download the module with Elixir’s Interactive Shell.
https://github.com/samratashok/ADModule/blob/master/Microsoft.ActiveDirectory.Management.dll
Download Microsoft.ActiveDirectory.Management.dll
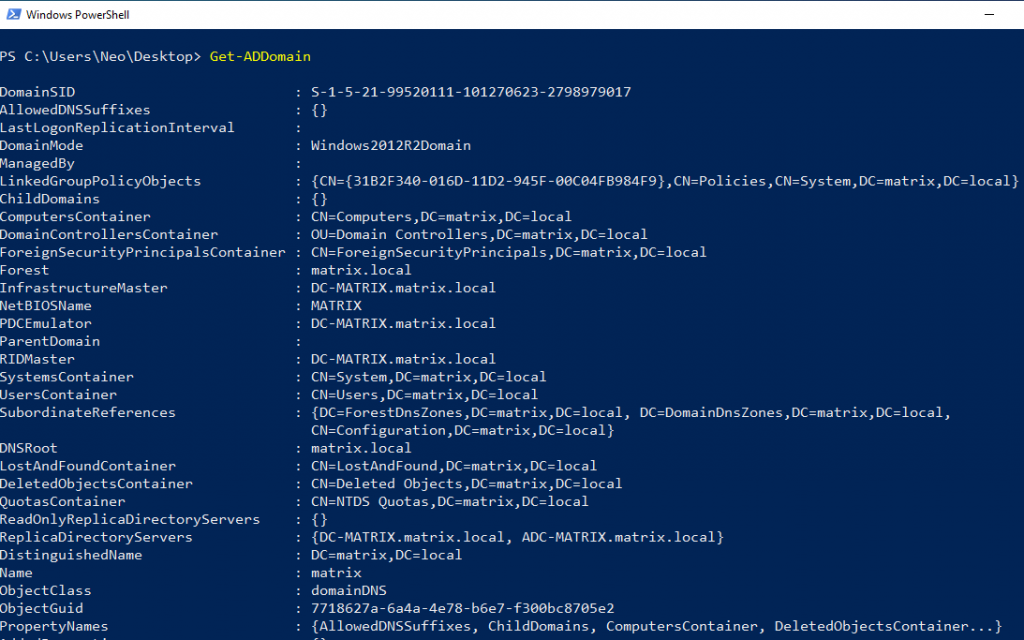
We were unable to use this command when the module was not installed. But now we can use… You saw the output given when querying with .NET. You can get more detailed information with this module.
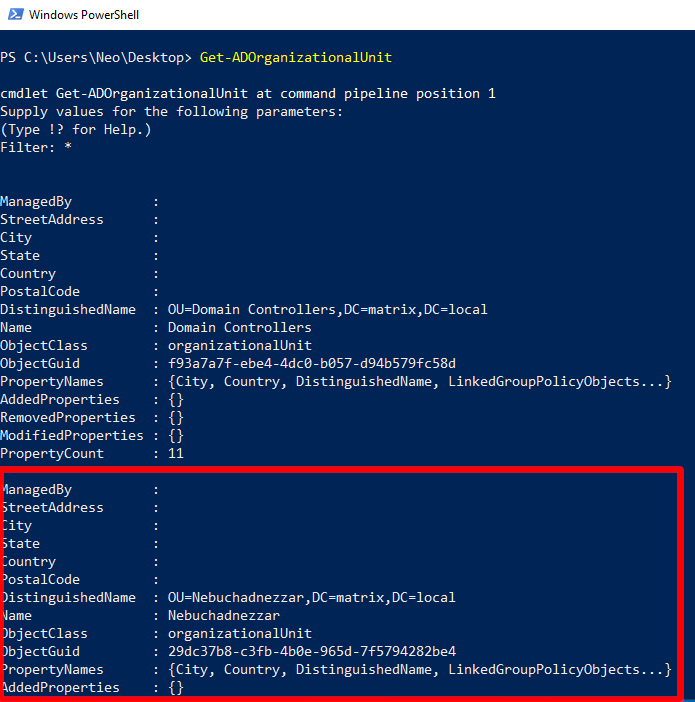
Let’s continue to analyze the group objects in the Active Directory structure…
We could detect these group names with wmic. But we do not know which Organization Unit these Groups are in. Organization Unit is a structure that contains objects such as users and computers. There is a remarkable name among the OUs analyzed…
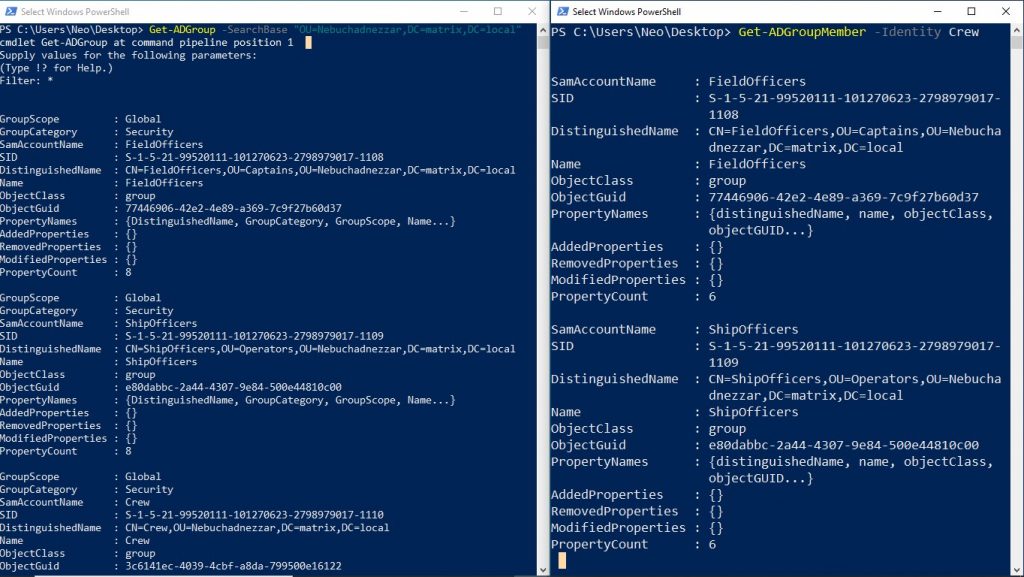
In the window on the left of the screen, the groups of OU detected are listed. In the window on the right of the screen, we see that there are groups when we list the members of the group named Crew. So if we assume a tree, Nebuchadnezzar OU is on top of it. Below it is Crew. On the branches of Crew, we can see FieldOfficers and ShipOfficers. I shared this tree in the previous post…
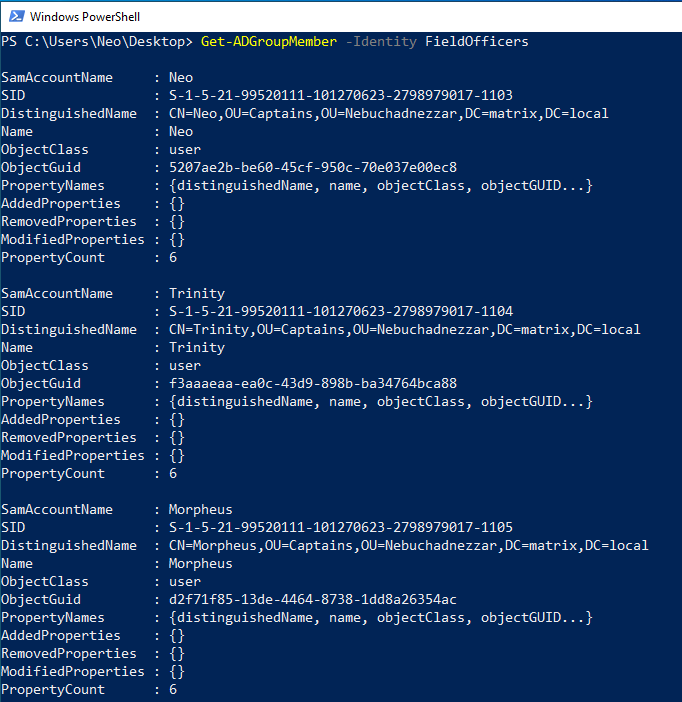
When you make the same query to a group, the objects that are members are listed. As an example, you see that members of the group object called FieldOfficers also have 3 users. The value written in the ObjectClass section indicates the type of the object.
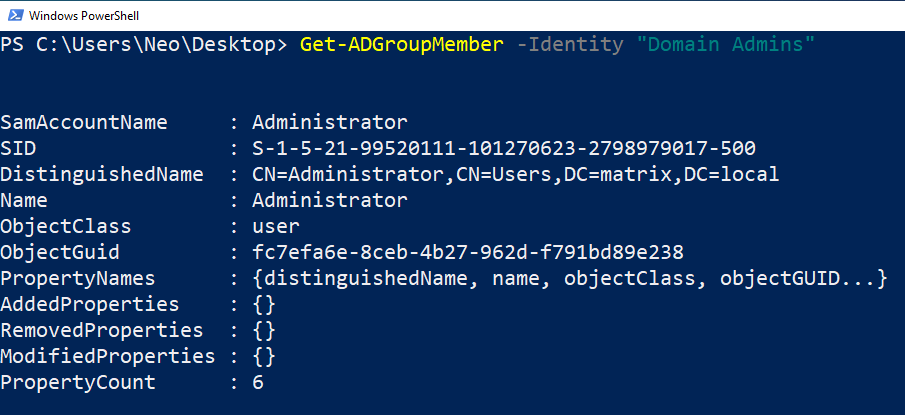
We have listed important users belonging to the Domain Admins group. Remember, with the user belonging to the Domain Admins group, you can control the entire AD structure.
Active Directory Powershell is a comprehensive module. In this article, I focused on Forest, Domain, Groups and Users and used basic commands. I think you understand the structure of the commands. Recon with PowerShell can be divided into several parts. I am already planning that in the future articles, users privilege, groups privilege and information gathering of group policies implemented in AD structure.
I apologize in advance if I am mistake or wrong. Please warn me in such cases. Don’t forget!
Knowledge increases with sharing…

